
The article describes a serious tendency in the exploitation of the word “scam” people, nothing of themselves representing.
Our group of companies has 350-400 customers on the ICO with a total collection of these customers at $ 2.5 billion and we often encounter one type question from our clients. They are written by people who allegedly found holes on the site, a smart contract, in other facilities. Of course, our customers (the founders of companies going to the ICO) are terribly afraid of this, they pay money to such fraudsters. In fact – this is a whole industry. Students and adults with a small IQ who have not found another job, use mass security scanners or simply fictional technical phrases to scare unsuspecting people. These are blackmailers in IT.
There are other not very intelligent people, they do not do this with blackmail, they just shout that all around are scammers. These Internet-woodpeckers are not interesting to consider, there are no dangers, they live in their community, where they stand out for each other, who better beat the word “scam”. Recently I was at CryptoShow – it was very unpleasant to listen to such “judges” when they trolled the founders of projects and arranged lengthy verbal skirmishes, showing their low qualifications. But the first group, who knows how to juggle with technical terms and use security scanners that really find problems (nothing threatening) is dangerous. These are real criminals, because make the founders of the ICO go with them to contact, waste time and eventually after pressure agree to pay money. Of course, this paragraph does not apply to those rare stories when a professional programmer found an extremely dangerous hole in an already existing large project (Facebook) and asked for money – legally, with proof, with silence about the found.
Typical portrait of the Internet-woodpecker: there is no big business, there are no known achievements, there are no large IT projects, but there are a lot of comments, video blogs or articles about what they think about this or that someone else’s ICO. Nothing else but a low IQ is not explained – people have not achieved anything, but on the negative they want to earn their fame. When a specialist in the ICO or IT industry has brains, abilities, intelligence, entrepreneurial veins – they spend their time on their projects and profits. For with scam-kakashek not much to earn.
A typical portrait of an IT blackmailer: a beginner or a former programmer, no interesting work or own projects, there are no personal prospects for an IT career. I learned to use other people’s holes (in security scanners) and I realized that now I’m something of myself. Unfortunately no. Of course, intelligent and talented programmers spend their efforts on their own projects.
I understand that it is impolite to write this way, but can’t found other words. Both groups of people are stupid. But due to the fact that they are loud-spoken fools, they are, in essence, heard.
What to do when there really is valid criticism?
Our group of companies and we in CryptoB2B are also engaged in criticism. But with significant differences, on a technological basis, massively, one can say scientifically.
For example, there is our rating agency ICOrating (different IT-woodpeckers sometimes criticize ICOrating, they say that this is scam too). What does the agency do? Has developed methodology, how to assess the business quality of an ICO. Employees of this agency in detail disassemble different aspects of their next client, who created ICO, and answer the main question – is it worth investing money there.
If the agency puts a good rating, this does not mean that the project will be successful. This means that such an ICO company is much more profitable than all other trash. And it’s more likely to earn money on the hype. It’s about probabilities and statistics. Of course, no one in my head will not write an unreasonable verbal diarrhe about fraud. The company has another goal – to make money. Their business colleagues, for example Matrix CIB, are engaged in related activities – they themselves invest money in the ICO. They need to know where to invest in their own means to multiply. Of course, Matrix traders are invested in tokens of those companies that have a good rating. By the way, if you are the founder of ICO and are looking for investments – contact me, we have a shareware service “search for investments for ICO” (payment of % on the money involved). So, IT-woodpeckers ohayivayut any projects, instead of creating their own (or because of insolvency to do their own). And absolutely sure of their rightness, because cook in the shallow community of the same losers.
The other side of the matter is technical. Where IT fraudsters or IT blackmailers are trafficked. When I personally have a valid criticism of the ICO, I take and conduct the code audit, with the proofs, pieces of code. And most importantly! With free advice on how to fix everything. This is the key word – to criticize and not say how to fix, automatically lowers the IQ of a person to 70. And lower. IT scammers are only aimed at short-term gain from the unfortunate founders of the ICO. Of course, scammers are profane in the areas of IT technologies that are affected by them, otherwise they would earn their living by a fairy-tale amount of money, working by profession!
The author of this article is engaged in on-line audit of smart contracts from customers for 1.5 years. Clients / funds come to us (in the rating or bank) and ask the question – can I invest in this or that ICO? Is the smart contract good? Is it safe? This is a private order, with a non-disclosure agreement, so the results are never published and there is no motive to lie, frighten, make no fables. In such reports only dry squeezes are written, that it is found, than it threatens, recommendations for correction. An example of such a public audit, where I disassembled the most popular ICO in July 2018 – https://cryptob2b.io/ubex-ico-security-audit/ If you slip something in another form – in front of you a scammer or an IT blackmailer. Yes, I understand that it takes time to compose a thoughtful audit. It’s much easier for an IT cheater to throw a couple of standard horror stories.
Note, my colleagues from ICOrating have given the Ubex project a high business estimate (+10 other rating agencies too). And this is not cheating, although Internet-woodpeckers claim that everything is paid for. And I put a sharply negative assessment that from a technical point of view, Ubex is a zero, not a project. Simply because both estimates are true at the same time, they can be rechecked, there is no collusion.
A fresh example of an IT blackmailer
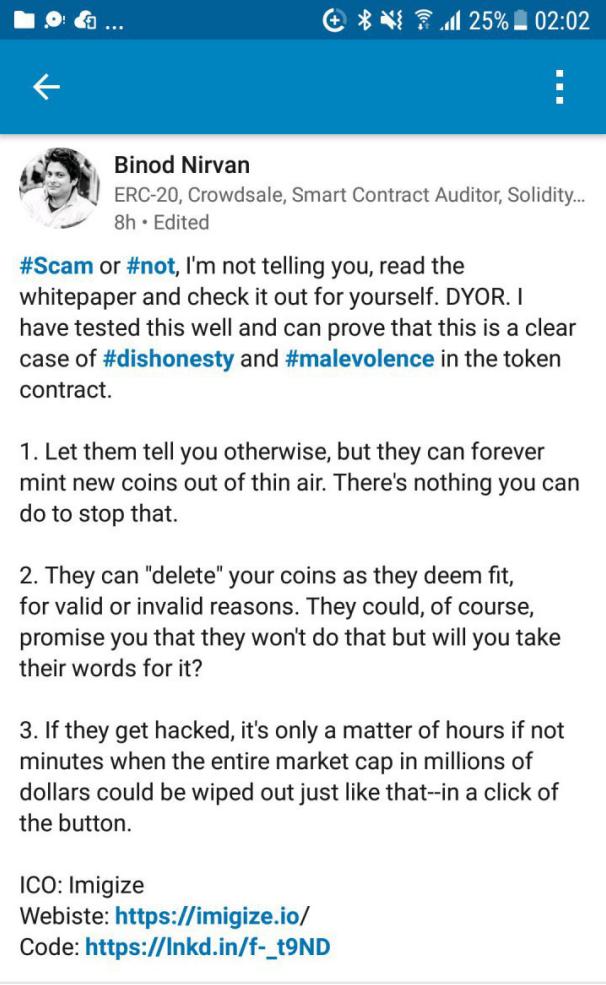
This is the screen of a man who smartly warns the unsuspecting public about the next “scammers” in ICO (although he himself is probably an IT scam). By his name in Linkedin you can find his profile and evaluate who it is – a real IT specialist, or IT-woodpecker, or an IT blackmailer who earns on such a specific topic.
The first problem of IT blackmailers is that it is very difficult to understand what they wrote. When such messages are read by the CEO of the company, he is very frightened of what he has written. And me, a programmer with 20+ years of experience, can not understand what was written. For this is a set of words, because I can assume too much. I do not argue, sometimes such IT blackmailers report real problems (+ payment request), which the security scanner revealed – it has a basis. But “vulnerability” is not worth the money requested, does not carry a big threat. Yes, it really should be removed and in fact in this case you need to pay a small reward, such as $ 50. Well, there is simply no reason to pay more to a student. Just there are just normal people who absolutely without any hints of money immediately report holes + details. It is reported with a detailed indication of what needs to be closed. For example, “You have on the site at http://example.com/backup/sql.zip there is an archive with all the passwords from the site”. There is no direct threat to the archive, but if you study the archive and try to apply the information found there – this is likely to lead to hacking the site. When they do not report details, they can not prove anything, they write general phrases – they are criminals classified as “IT blackmailers”. It was a generalization – about the general statistics that I collect from my clients. In particular, in this example with Binod, he does not write about money, but this is only the first message, and does not reveal examples at all. If he says that you can hack – so crack first, then write!
The second problem. Unfortunately, both Binod and all the other critics do not tell how to do it differently, correctly, ideally. Let such a writer show his PERSONAL code of an ideal smart contract, and then I’ll either arrange a big expository review of Hindu programmers (in Russia there is a non-politically correct meme about the “Hindu code”), or I’ll apologize + say thank you + I’ll learn something myself + I’ll fix it myself my mistakes + I will teach others this. I built my ICO platform and smart contract code, spending 1.5 years auditing and reading really horrendous code all this time. In my story, only 5% of clients had no problems and we gave them a positive conclusion. Of course, in the near future I will go and look at that level of ICO, where the author of the words from this screenshot takes part (Binod is an adviser in the ICO series). According to my personal statistics, in 90% of cases the code of the smart contract will be beyond hell, where absolutely everything is violated, starting with the main ideology of the detachment.
The third problem arises from the lack of experience of Binod and its low legal base for serving projects during the real life after the ICO (I recall our experience in the ICO – more than 350 clients). The second paragraph is written in a false way to scare someone, but it has grounds for legal problems. If in the course of the life of the project in some country a judicial decision (or one body) decides on the tokens relative to some personal investor, then the responsibility for the execution will lie with the company. Accordingly, this is not the removal of the tokens (no removal, Binod is lying) than frightening the IT scammer, and freezing the tokens for reasons that are not independent. It is also used for investors who maliciously shy away from the KYC procedure for a long time. In these cases, the company conducting the ICO is required to roll back the transaction: token freeze (or delete, although no removal) and return the money. Frost also implies the abolition of freezing. For example, if the court overturns the first decision, then the freeze is simply canceled.
Fourth. Binod writes that if something is hacked there, then the end of the world will come. I’m sorry, but what about such people in my head? After all, the same thing can be written about anyone: if all planes are hacked – you all will die. And who does not fly – do not relax, too, will die from falling suitcases. If you hack all the iPhone – you all will die without the Internet and the ability to read stupid articles on the topic “ICO – solid scam”. Such arguments are possible for schoolchildren. As for breaking into a smart contract, you can not hack it. Generally in any way (99,999%). I invite Binod to hack my smart contract and steal the tokens. I periodically lecture on errors in the ICO, so, my first first point about the bugs there just about breaking. But I immediately reiterate that a really direct hacker threat to a smart contract is the most incredible event. For a programmer to leave a hole, this is an extremely rare situation, but in theory it is possible. Do not leave holes – it’s very easy. Even for a bad programmer. Any true auditors of smart contracts know this. Yes, smart contracts have problems that lead to loss of money. For example, personally, with my programmers, I saved money from direct damage by $ 70 million (by conducting an audit of someone else’s ICO). But there was never a hole, so that the hacker could steal something. There were other kinds of mistakes. Total, if some “expert” writes that a hacker can crack and further colorfully describes the consequences – it’s a layman. Often, there are tragedies when a smart contract can break by itself through the fault of programmers, while the money hangs tightly, they can not be obtained by anyone (neither the hacker nor the founder). This problem is real. Of course, it is also not in the ICO under discussion – I simply explain to the public about the dry statistics that happens in smart contracts.
Fifth. Binod writes that you can release any number of tokens. He is probably used to dealing with bad ICOs (I also hate them and criticize them), but in this case the charge is deceitful. In a smart contract there is an honest softcap + hardcap. Honest is the key word. Based on their personal experience of analyzing someone else’s ICO, very often (> 70%) investors are promised a softcap or / and hardcap, but in practice (in the code) it does not exist. I agree with this point, it happens. With this you need to fight! But at Imigize it is not present, do not lose a head and do not row all under one comb.
The sixth. He writes something about capitalization. Like, if a hacker presses a button (which he did not press so far?), Investors will suffer. Apparently, the author of words is far from reality. On such an incredible case for a long time there is a simple solution. Suppose all tokens are stolen. But in the detachment, everything is recorded. We remove the register by owning the tokens at the time 5 minutes before the hack. We issue new tokens on this register, we send out. We all declare: we were hacked, but the problem is already solved, do this and that (instruction how to see new tokens in the purse). That’s all. Yes, it’s very unpleasant from a marketing point of view, the company’s image suffers, but no more – no damage. It is only in the head of IT blackmailers.
Seventh. This ICO does not apply, it affects the general logic, which, due to lack of IQ, is inaccessible to many critics. What is Imigize? This is a non-contact shoe fitting. New technology. This project and technology exist by themselves, do not depend on ICO (which is necessary to raise money for industrial centers and advertising). What do critics see as scam? In that there was an innovation, when in shoe shops online you can buy shoes, being sure of the right size? And how does the critic comment that you can come to the store legs, scan your foot and buy shoes in the online store? Critics against really new technologies, which literally can be felt with their feet? I think the answer is obvious – the critics have something wrong.
Eighth. If you have a desire to audit something (or yourself or an object of future investments), then of course, we will be happy to conduct any audit – code analysis, technical analysis of white paper, is there at all any hints at all about the structure project, except juggling with the words “blockchain,” nothing to say, but very beautiful flowcharts and charts. Of course, the work will be done in an academic style, various implicit aspects of the behavior of the smart contract are explored. Contact CryptoB2B. For example, due to Ethereum’s general shortage and wretchedness (other blockchain systems are even worse) and especially development / debugging / testing tools, we sometimes rewrite the code for Solidity to another language (PHP / JS). This allows you to drive millions of tests in dozens of minutes. The same test in tools from the Ethereum community would take years or the programmer would simply be too lazy to do it. Of course, we do not write low-grade reports and do not frighten us with threats, in the style of “analysis” that you saw in the screenshot.
Total, the sequel follows in the form of separate articles, I need to study the creative activity of this gentleman in order to evaluate his achievements in the ICO and other projects … This was an example of an advanced IT blackmailer. Usually, their messages are even less professional, more childish, there is nothing to review and comment on there. Thanks Binod for the opportunity to write an entire article. It’s been a long time ago (the general low technical level), but there was no reason to speak. Of course, this was a private appraisal of the author, and not an official response of anyone to anything.
Author of the article: Dmitry Borodin, (co)founder: CryptoB2B.io, Topface.com, Imigize.com, php.spb.ru.
We apologize for the English version of the article – translated into Google.
UPDATED: A fascinating continuation of this story is here, part #2: https://cryptob2b.io/comments220718/